← Go back
Comprehensive Guide to Code Security Audit: Ensure Software Integrity


In a world increasingly driven by software, the importance of maintaining robust security protocols in code cannot be overstated. At Pieoneers Software Inc., we recognize this imperative and dedicate ourselves to the meticulous practice of code security auditing. This guide delves into the nuances of this crucial process, combining insights from our experiences with the Jevitty Life Sciences app and Bodycomp Imaging technician platform.
Understanding the Essence of Code Security Audit
Definition and Importance
Code security audit involves analyzing source code to uncover vulnerabilities and security flaws. It’s an integral component of software integrity and crucial for safeguarding sensitive information. In an era where software underpins many aspects of our lives, ensuring its security is a technical necessity and a foundation for digital trust.
Dependencies and the Bug Dilemma
Modern software, whether a concise script or a complex program, often relies on additional libraries. These dependencies facilitate development and expand the code base and potential for bugs. Given that humans, prone to error, write code, achieving entirely bug-free software remains an elusive goal.
Audit for Vulnerabilities
Regular penetration tests, while valuable, are time-limited and unlikely to uncover all security issues. The black box approach, often adopted due to budget constraints, further limits the depth of software auditing. Cybercriminals, unrestricted by such constraints, have ample resources to analyze software for exploitable flaws.
Difference Between Security-Focused and Quality-Centric Code Reviews
When we speak of code reviews within the development lifecycle, it’s crucial to distinguish between two distinct objectives: ensuring code quality and fortifying security. While traditional code reviews aim to validate code for maintainability, readability, and performance, security code reviews focus on different criteria.
Prioritizing Security in Code Reviews
In a security code review, the spotlight shines on the secure aspects of the codebase. This includes but is not limited to, scrutinizing database operations, validating authentication protocols, and examining configuration settings. The goal is to identify security bugs—those specific software flaws that could lead to unauthorized actions and, by extension, security breaches.
A Dual Approach to Security Code Reviews
The methodologies applied in security code reviews are two-pronged:
Manual Reviews offer a meticulous, human-led examination of the code. This method relies on the expertise of seasoned developers or security professionals to dissect complex code logic and detect subtleties that automated tools might miss.
Automated Reviews leverage advanced tools to scan vast swathes of code efficiently. This process can quickly uncover a broad spectrum of known vulnerabilities with minimal human intervention.
Adhering to Security Standards and Employing Tools
Security code reviews gain structure and direction by adhering to recognized standards and utilizing specialized tools:
Standards to Guide Security Code Reviews:
- OWASP TOP 10: A crucial benchmark for web application security.
- Mitre Top 25 CWE: An exhaustive list detailing common software weaknesses.
- PCI-DSS: A mandatory standard for entities handling credit card transactions.
- HIPAA: The compliance framework for protecting patient health information.
- PIPEDA: Canadian data privacy law governing personal information handling.
Automated Tools to Enhance Security Code Reviews:
- SAST (Static Application Security Testing): These tools dissect code patterns to find security discrepancies and are tailored to specific programming languages.
- DAST (Dynamic Application Security Testing): DAST solutions analyze running applications, independent of the code’s language, to pinpoint runtime vulnerabilities.
- Incorporating SAST and DAST into the S-SDLC
SAST tools fit within the Secure Software Development Life Cycle (S-SDLC), offering developers early alerts to potential security flaws.
DAST tools, on the other hand, require operational instances of applications for testing, providing a crucial post-deployment safeguard. However, they necessitate a nuanced understanding of the results to mitigate discovered vulnerabilities effectively.
By integrating these methodologies and tools, developers can construct a robust defence against the ever-evolving landscape of cyber threats.
Application Audit in Healthcare and Life Sciences
For entrepreneurs in the healthcare and life sciences, understanding the web and mobile application audit is more than a regulatory checkbox—it's a cornerstone of business integrity. Health and life sciences applications handle highly sensitive data, from personal health information to proprietary research data, which demand adequate security and privacy compliance.
Here are the key considerations that healthcare and life sciences entrepreneurs should keep in mind:
Regulatory Landscape
Familiarize yourself with the regulatory framework specific to your target market. In the United States, HIPAA compliance is non-negotiable, while PIPEDA sets privacy standards in Canada. The European Union's GDPR is another critical regulation that has global implications. These regulations dictate stringent data protection and privacy measures, making an in-depth code audit indispensable for compliance.
Data Sensitivity
Healthcare applications often deal with data that is both personal and sensitive. This data requires encryption at rest and in transit, and access must be tightly controlled and logged.
Data Encryption and Access Control
In healthcare apps, data isn't just sensitive—it's deeply personal. We prioritize robust encryption and meticulous access logging. This ensures the integrity and confidentiality of each data transaction.
Complex System Integration
Our apps often interface with systems like EHRs and LIMS. Each integration is a potential security risk, rigorously audited to ensure a fortified ecosystem.
Adaptive Compliance
In the ever-evolving healthcare regulatory landscape, our audits are continuous. We adapt swiftly to changes in regulations, ensuring enduring compliance and security.
Robust User Access Controls
We implement multifactor authentication and role-based access controls as standard practices. These are critical in safeguarding user interactions within our applications.
Proactive Vulnerability Management
Our approach is preemptive. Regular updates and patches are part of our routine, keeping our systems resilient against emerging threats.
Continuous Risk Assessment
Risk assessment is an ongoing process. It informs our audit strategy, helping us prioritize critical reviews and maintain the highest security standards.
Vendor Compliance Management
Third-party integration requires stringent vendor compliance. We ensure all external services meet our high security and regulatory adherence standards.
Incident Response Preparedness
Our incident response plan is clear and tested. We're equipped to handle security incidents effectively, including necessary breach notifications.
Building Patient Trust
Our ultimate goal is earning patient trust. Rigorous audits and stringent security measures are about more than compliance—they're about building a trustworthy healthcare ecosystem. In this way, we don't just build applications; we build trust.
Healthcare and life sciences entrepreneurs must adopt a holistic and vigilant approach to application auditing. By prioritizing security and compliance from the outset, you can avoid costly mistakes, protect your users' data, and ensure that your application stands up to the scrutiny of regulatory bodies and the market.
Case Studies of Audit in Healthcare and Life Sciences

- Continuous Integration and Deployment (CI/CD). Agile CI/CD framework was implemented for regular, secure updates and patches, ensuring the app remains resilient against emerging security threats.
- Multifactor Authentication. Multifactor authentication is a vital layer of defence for protecting sensitive health data, reinforcing the app's adherence to stringent security protocols.
- Google Firebase Utilization. We chose Google Firebase, a decision instrumental in aligning with HIPAA compliance standards, thus fortifying the app’s commitment to safeguarding patient data.
Case Study: Jevitty Health & Wellness App Development
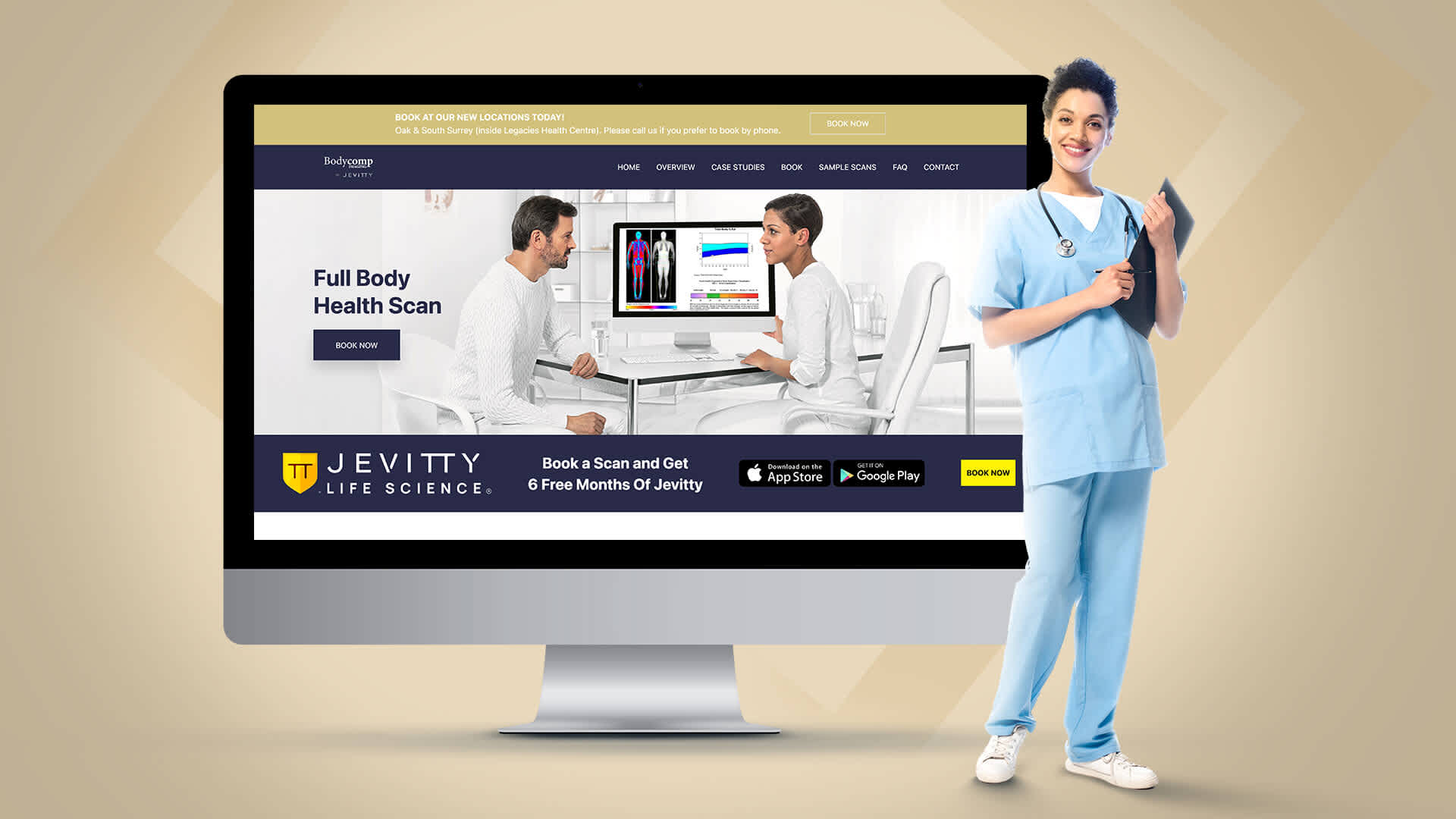
- Secure Patient Information Management. We developed a platform that prioritizes the secure handling of patient data, implementing advanced encryption and access control measures.
- Two-factor Authentication. We incorporated two-factor authentication, significantly enhancing data security and mitigating unauthorized access risks.
- Seamless API Integration with Jevitty App. Secure and efficient API integration was needed facilitating cohesive and protected data exchange within the healthcare ecosystem.
Case Study: A Seamless Integration of Body Composition Scanning Services with Jevitty App
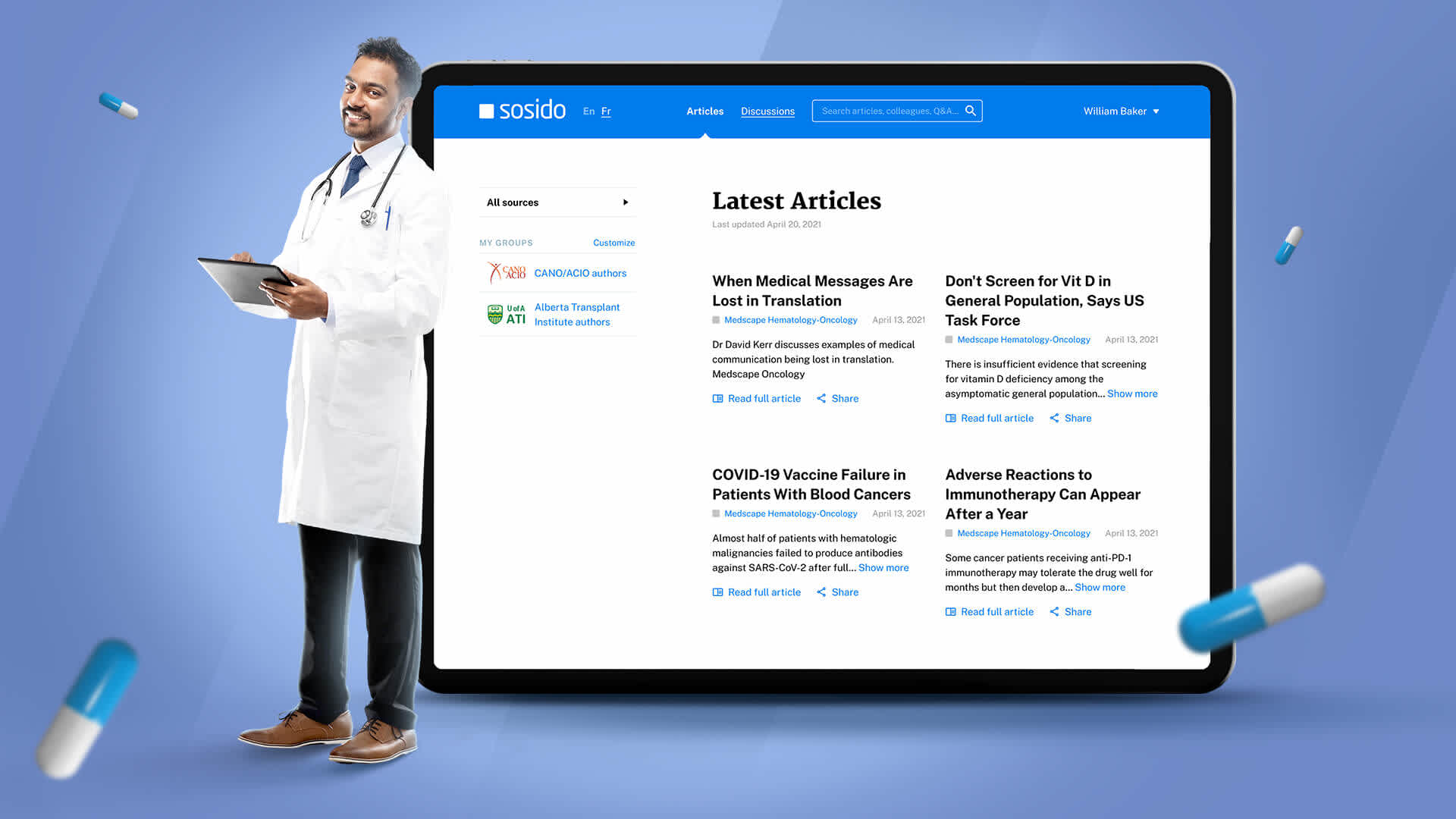
- Robust Technology Stack for Enhanced Security. Pieoneers helped Sosido transition to a more secure and robust technology framework with AngularJS, PostgreSQL, and Heroku. This update bolstered the application's defence against potential security vulnerabilities, ensuring a safer platform for healthcare information exchange.
- Streamlined and Secure PubMed Integration. We implemented a secure and efficient integration with PubMed.
- User-Centric Secure Features for Enhanced Engagement. We rolled out new functionalities, such as personalized news feeds and discussion threads, focusing on security.
Case Study: Elevating Healthcare Information Sharing - The Sosido Web Application Revamp
These case studies provide real-world examples of how security and compliance principles are applied in healthcare app development.
Sensitive Data and Configuration Files
Reviewing configuration files is critical. Sensitive data stored in code repositories is considered compromised, necessitating secure storage solutions like vaults.
When sensitive information, such as passwords, API keys, or personal data, is stored directly in code repositories, it's at risk of exposure and considered compromised. Using safe storage options is essential to reducing this danger. These include encrypted data vaults or environment-specific configuration management systems that separate sensitive data from the codebase.
Implementing role-based access controls and updating credentials regularly is equally crucial. These are essential procedures that further protect sensitive information. Regular scans for exposed secrets in code repositories should be conducted to identify and promptly address any security lapses.
This comprehensive approach ensures that sensitive data is stored securely, managed and accessed in a manner that upholds the highest standards of data security and compliance.
Concluding Thoughts
Code security is of imperative importance. Reviewing software code is challenging yet vital. The key insights highlight why a thorough code analysis to identify vulnerabilities and a balanced approach combining manual insights and automated tools is needed.
For healthcare and life sciences entrepreneurs, understanding the intricacies of regulatory compliance, such as HIPAA and PIPEDA, is paramount to ensure their applications meet stringent data protection standards.
At Pieoneers, we work to uphold the integrity of the digital ecosystem in every project we undertake. As a CTO, I commit to this comprehensive approach, ensuring our software is functional, secure, and trustworthy.
Protect your software from vulnerabilities and build trust with secure and reliable applications.

Andrew Manshin
Pieoneers CTO